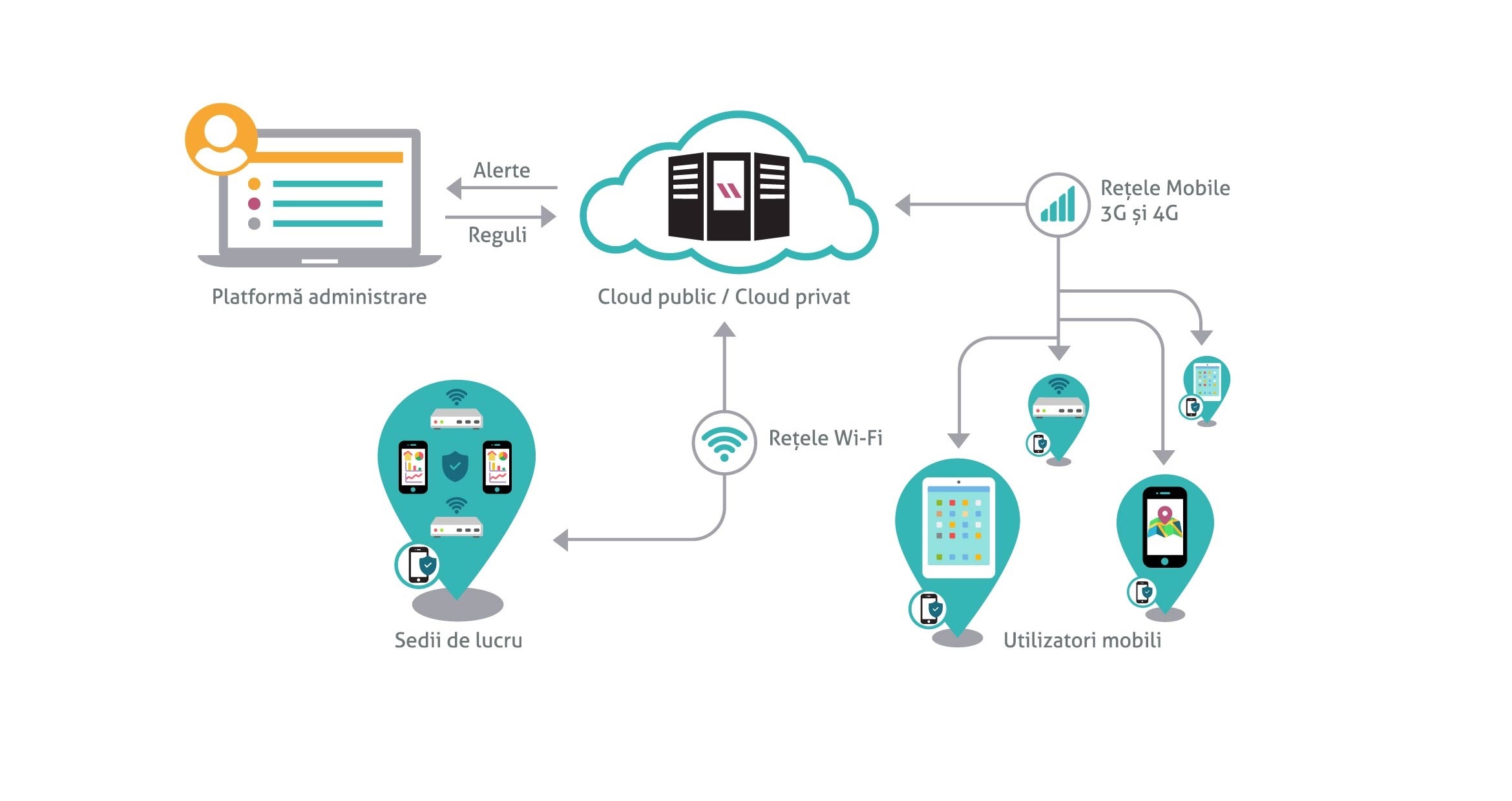
Mobile Device Management
With Mobile Device Management, you can manage and secure your mobile assets and set them on autopilot.
It helps provide a consistent user experience throughout your organization, while empowering your mobile workforce and optimizing IT overhead.
Our Mobile Device Management solution allows remote administration and configuration of mobile or fixed remote assets, as well as preventing employees from using devices other than intended.
Work Scenarios



Deploy • Manage • Secure • Monitor with
Bento Mobile Device Management
Get rid of the stress of having to constantly manage your mobile devices by automating the mobile device configuration process in your company.
Features

The Management
Platform
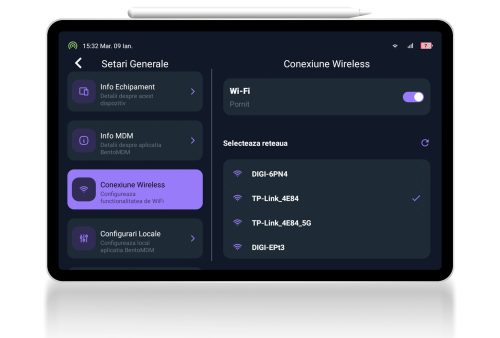
OTA (Over The Air) enrolment
Automatic device configuration based on profiles
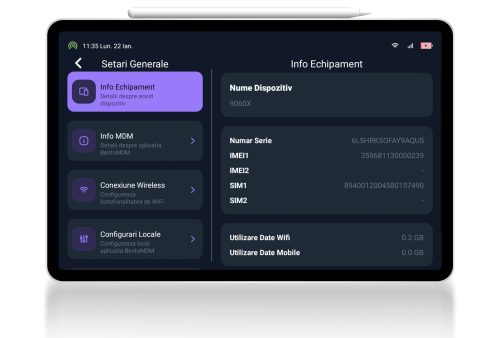
360-degree view of all devices configured in the system
Mobile App management
Content management
Security enforcing
Centralized user management and access security
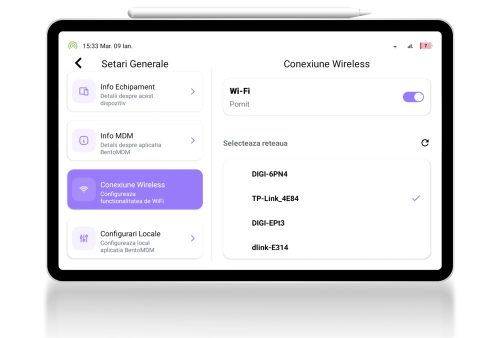
Remote device management
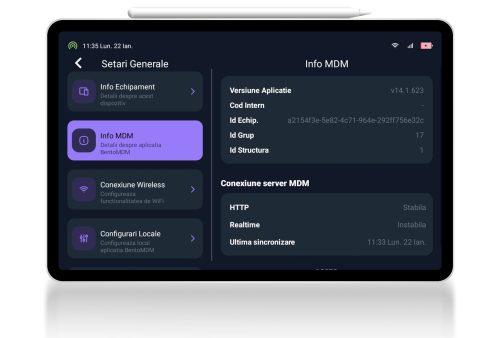
Audit and tracking reporting
Deployment of restrictive user experience
The Management Platform is used by dispatchers, IT managers, mobile fleet administrators and unit managers.
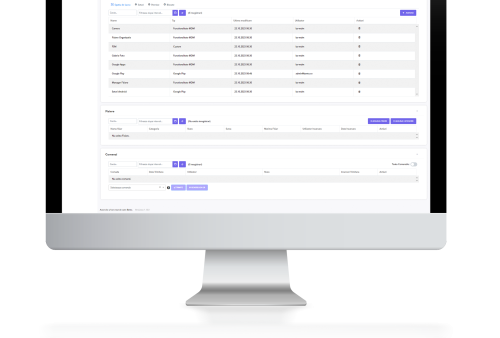
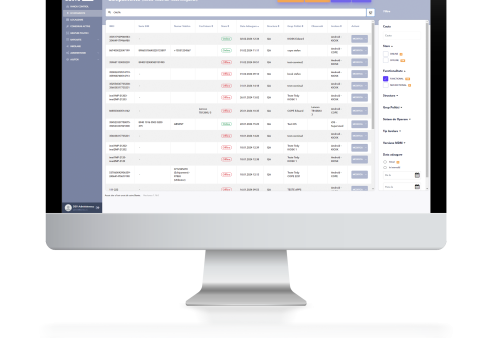
This is the “office” component – an unified console to manage and track all different assets.
This administration platform delivers easy-to-use remote centralized management of mobile and device fleets. It integrates several automation features and provides all necessary functionalities in a good looking package.
The admin console also enables the IT team to manage policies, updates, features and security.
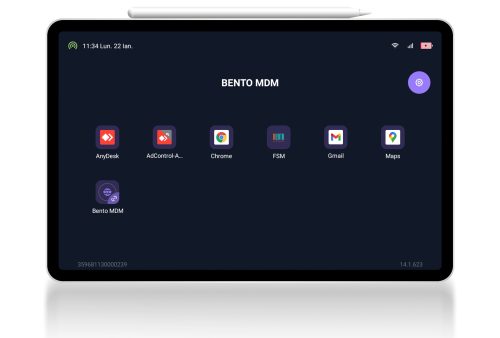
Mobile app
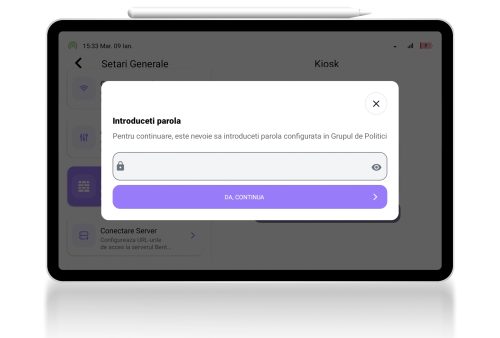
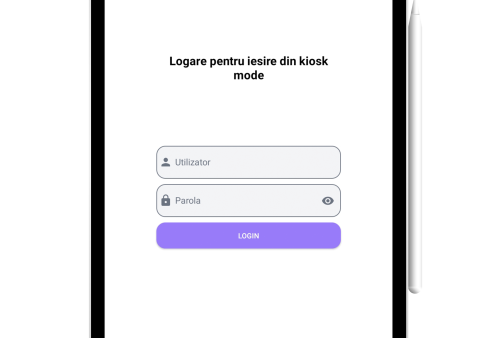
Kiosk mode
Credential based login
Automatic synchronization of offline data when the app goes online
Update management of OS patches, Apps and system features
Restriction of user access OS and UI elements
Policy and security restriction enforcement
App and feature access restriction
Mobile App running silently on devices
The mobile app is the enforcer on the field. When set to Kiosk mode it is used to provide access only for approved Apps, based on profiles and specific user rights. It also limits OS features and system Apps and enforces policies and security restrictions.